Lesson 2 of 62By Baivab Kumar Jena
Cybersecurity is a popular topic, but do you know why it is essential? We are living in a digital era where data is everything. We must understand that private information is much more vulnerable than ever before. We often hear about data breaches and cases of identity theft that affect millions of consumers. Two years ago, WannaCry ransomware encrypted millions of computers. All companies and institutions are fighting to protect their data against hackers and cybercriminals, and you can also play a role in it. Cybersecurity is not involved only in organizations, but even personal computers, mobile phones, and tablets.
Before we begin learning this cyber security for beginners tutorial, let us first understand what exactly is cyber security and what is its significance. Cybersecurity is the technology and process that is designed to protect networks and devices from attacks, damage, or unauthorized access. Cybersecurity is essential for a country’s military, hospitals, large corporations, small businesses, and other organizations and individuals since data is now the cornerstone of any organization. If that data is exploited, then there are a lot of risks. Now, we have understood what cybersecurity is, let’s see what the CIA triad is and how it is related to cybersecurity.
The security of any organization starts with three principles: Confidentiality, Integrity, Availability. And next in this cyber security for beginners tutorial we will learn about the CIA Triad, which has served as the industry standard for computer security since the time of first mainframes.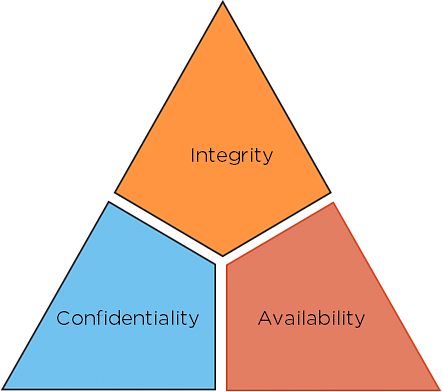
Fig: CIA triad
Next up in the cyber security for beginners tutorial, let’s look at the areas and speciality in cybersecurity to understand the space better.
To pursue your career in cybersecurity, it is essential to know about the areas of specialization in it, and this cyber security for beginners tutorial will help you do just that. There are nine:
A cyber security bootcamp provides hands-on experience and theoretical insights, allowing individuals to uncover their specific interests and strengths. By focusing on these specialties, participants can enhance their skills and knowledge, preparing them for roles that demand expertise in specific aspects of cybersecurity.
Next up, this cyber security for beginners tutorial will help you understand some of the terminologies you must be familiar with before learning anything about cybersecurity.
A network is a connection between two or more computers so that they can communicate with each other. For example:
Fig: Network Connection
Internet is a means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers.
The data that is transferred or received cannot follow any path. There are a set of rules that are followed to control the flow of the internet. These rules are called internet protocol.
An Internet Protocol address (IP address) is an address assigned to all devices that connect to a computer network and uses the Internet Protocol for communication. An IP address looks like this: 168.192.10.3
This is a unique identification number that every device has that connects to the internet. Traditional MAC addresses are 12-digit hexadecimal numbers. MAC address looks like this: D8-FC-93-C5-A5-EO.
Consider DNS as the phonebook of the internet. All the IP addresses and the name of the links are saved in it. For example, you want to go to google.com. You type this on your web application. Then, this name goes to the DNS server, and the DNS server finds the IP address of google.com. Then, the DNS server returns it to your computer with the IP address.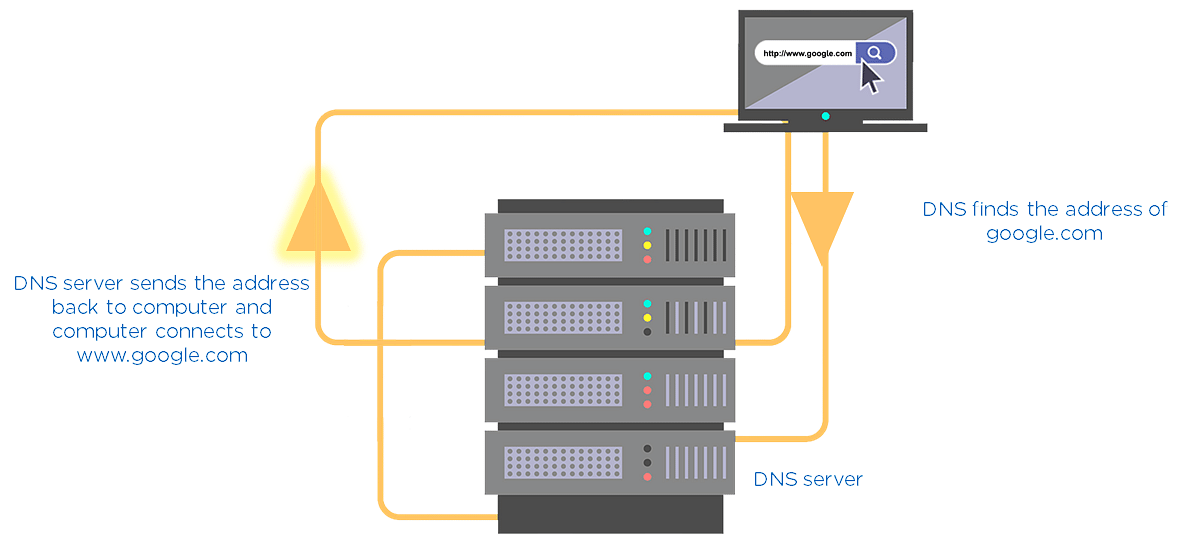
Fig: DNS Server Illustration
Dynamic host configuration protocol is a protocol that assigns an IP address to any device that wants to connect to the internet.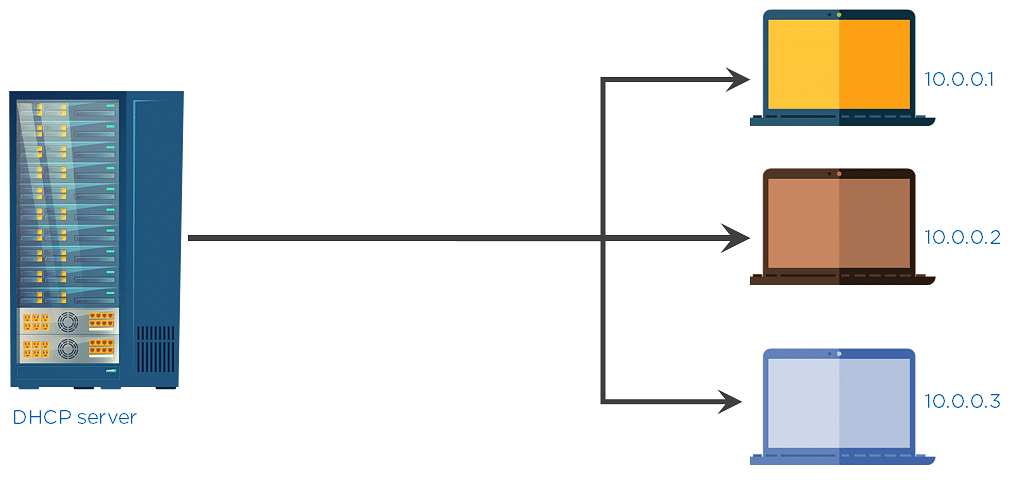
Fig: DHCP providing IP addresses
This is a device that routes the data that comes to it and then sends that data to the destination to ensure that it is on the appropriate path.
Bots are computer programs that control your computer without your knowledge. They automatically send emails, retrieve web pages, and change computer settings.
Before we get into the types of attacks, we should know why these attacks happen, and this cyber security for beginners tutorial will help you learn A-Z of both. There is always a motive behind every attack; the main reason for attacks is money. Hackers penetrate the system and then demand ransom from the victims. There are other reasons like a financial loss to the target, achieving a state’s military objective, damaging the reputation of the target, or political maneuvering.
There are mainly five types of attacks:
In the next section of this cyber security for beginners tutorial, let’s look at all the attacks in detail:
It is an attack used to restrict a user from accessing the resources by flooding the traffic that is used to access resources. A botnet controller controls all the bots that are under it. The attacker sends a command to the botnet controller that tells all bots to attack a server so that the server will be flooded. When a user wants to access a website, he will not be able to, as the traffic on the website will be at full capacity.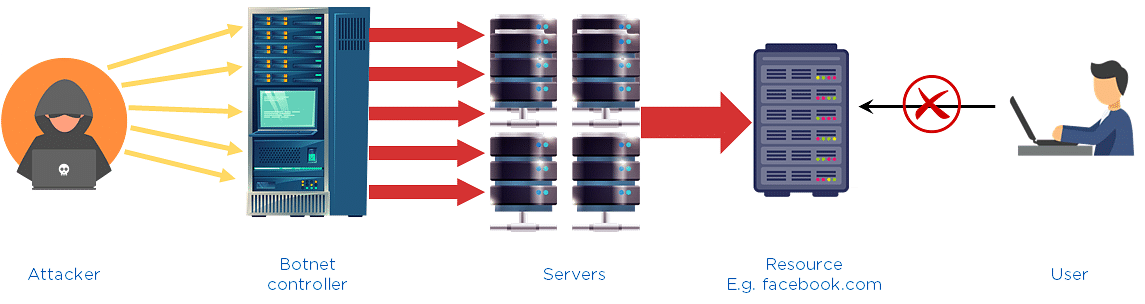
Fig: DDoS Illustration
Let’s look at an example to understand this better. Suppose you want to do an online transaction and you connect to your bank and make the payment.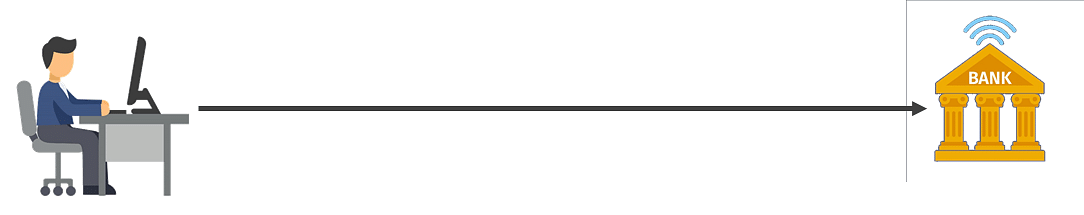
Fig: Man in the middle attack (1)
Now, while you are completing the transaction, you have to put in credit card details and the PIN. The attacker can spoof you and monitor your transaction. As soon as you put in your details, he will see them.
Fig: Man in the middle attack (2)
To crack a password or find a password, we use this technique. There are five types of password attacks:
First, let’s see how an email works. Suppose John is sending an email to Jack. The email first goes to the email server. Then it goes to the DNS server to find the IP address of the destination. From the source email server, the email goes to the destination server. From there, the email is sent to the IP address on which Jack is working. It is illustrated in the picture below.
Fig: How email works.
There are three types of email attacks.
Download these attachments only if you are sure that it is a legitimate email.
The kind of job you do is definitely something you wish to consider before you step foot in any field. In this section of the cyber security for beginners tutorial, we will learn about top roles in the cybersecurity field:
What did you learn from this cyber security for beginners tutorial and how much do you know about security concepts? Take up this CISSP Practice Exam and test yourself.
To start your career in the cybersecurity field, you must know the certifications that you need to clear to get into this field. Wondering what are they? This cyber security for beginners tutorial has got that covered for you too. The top three certifications are:
Check out the below video, to sum up this tutorial on cybersecurity –
There is substantial evidence that cybersecurity is in demand right now. This demand will continuously grow, and it is challenging to measure labor supply or demand in this field. The primary reason for growing this field is that technology is improving every day. It is good that the whole world is working together to reduce cyberattacks because of the economy and communication across the globe. cybersecurity is a complex subject that requires knowledge and expertise from multiple disciplines but not limited to computer science and information technology.
This cyber security for beginners tutorial covers everything you need to know about the fundamentals, basic terminologies, and certifications too. And if you think you’re ready for a challenging yet exciting field like cybersecurity, you must check out Simplilearn’s comprehensive Cybersecurity Training program, that covers everything from cyber security for beginners to advanced networking skills you need to build a successful career!
If you’re interested in learning more about cybersecurity, check out Simplilearn’s comprehensive Cybersecurity Training program.
Baivab Kumar Jena is a computer science engineering graduate, he is well versed in multiple coding languages such as C/C++, Java, and Python.
Cyber Security: Career Path | Skills | Salary | Certifications
An Introduction to Cyber Security: A Beginner's Guide
Cyber Security Bootcamp: The Fast-Track to Becoming a Cyber Security Professional
Fuel Your 2024 Cyber Security Career Success with the Caltech Cyber Security Bootcamp
Types of Cyber Attacks You Should Be Aware of in 2024
How to Build an Enterprise Cyber Security Framework
© 2009 –2024– Simplilearn Solutions
Follow us!
Company
Work with us
Discover
For Businesses
Learn On the Go!
Trending Post Graduate Programs
Trending Bootcamp Programs
Trending Master Programs
Trending Courses
Trending Categories
Trending Resources




