Official websites use .mil
Secure .mil websites use HTTPS
The internet is a source of infinite information, but not everyone who creates content is reputable. The web is rampant with individuals and entities who wish to do harm.
Information leaks, blackmail, ransomware, fraud, and financial ruin are a few of the possible hard realities of cybercrime. However, it’s the human element that is the best defense against digital attacks.
“There are still things that technological safety nets can’t do,” said Randy Miller, Chief Information Security Officer, Headquarters, Air Force Materiel Command. “AFNET [Air Force Network] users must practice safe cyber hygiene techniques to keep our network safe.”
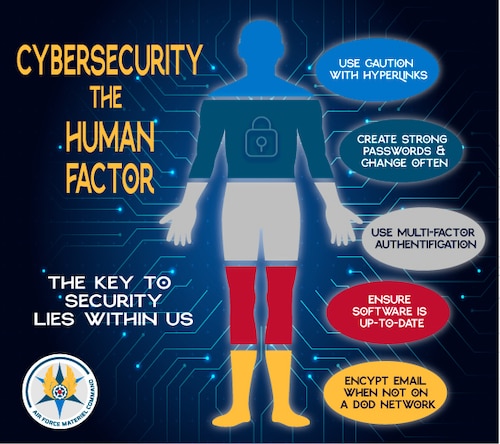
Some of those techniques include using caution when accessing unfamiliar hyperlinks, creating strong passwords, leveraging multi-factor authentication, and ensuring software is up to date.
These techniques are important not only for the Department of Defense, but also at home.
Infographic of the areas humans can control in cyberspace
First, individuals need to think carefully before accessing hyperlinks. More than 90% of successful cyberattacks start with a phishing email or text that includes a hyperlink.
Before opening any hyperlink to verify personal information, consider the source. Hover over the hyperlink to determine if it is from a legitimate sender. Many phishing attempts are very sophisticated and try to impersonate people whom individuals know.
Good computer hygiene requires individuals to verify the source before offering information or accessing a hyperlink, especially if the email is coming from a non-DoD sender.
Another key area of vulnerability concerns password use. Addresses, birthdays, or using the one password most dreaded by cyber security experts, PASSWORD123, can make accounts susceptible to attack. The use of memorable passphrases, crafting unique passwords for individual sites or applications, and passwords that are at least 15 characters long and use a combination of numbers, special characters, and uniquely spelled words are the least vulnerable. Password Managers offer the best defense against password cracking by cyber criminals.
“Since a lot of people telework, home networks should also be protected,” cautions Miller. “Make sure you change the password on your home router regularly using a strong password and follow the security guidelines set forth in the AFMC Telework Guide.”
The DoD relies on multi-factor authentication to protect networks on many applications. MFA is simply adding an extra step after the username and password to gain access to an app. This is enforced in the DoD with the use of a CAC card and a PIN. Many private .com sites offer various MFA options, including a PIN, a confirmation code sent to phones or email, or face or fingerprint recognition.
Finally, up-to-date software is also a critical computer hygiene requirement. Developers push out security updates almost daily to defend against cyberattacks. Rebooting DoD devices daily also keeps security updates current.
DoD has made recent changes to make email encryption easy for users. DOD regulation (DoDI 5200.48_DAFI 16-1403) requires all controlled unclassified information (CUI) transmissions be encrypted. Emails sent on the DAF networks (@us.af.mil, @usspacecom.mil, and @spaceforce.mil address) are already encrypted. The Office of the Air Force Chief Information Officer (SAF/CN) has distributed guidance stating that only CUI emails going to non-DAF email address enclaves must be encrypted before sending in Outlook.
The introduction of the Controlled Unclassified Information (CUI) Program has brought on some confusion among DoD employees. CUI replaced the use of “For Official Use Only” on documents containing critical information. In any case, CUI documents must be properly marked and accessed only by those with a need-to-know.
“Not all legacy marked “For Official Use Only” (FOUO) documents are now CUI. It is not an automatic one-to-one swap,” said Miller. “Some information previously marked as FOUO will qualify as CUI, but FOUO information must be assessed against the CUI Registry to determine if it is now CUI.”
October is Cybersecurity Awareness Month, but employing a security-centric mindset should be an everyday practice and not just once a year. Cybersecurity hygiene is a critical daily need both in the workplace and at home.
Threats evolve and change quickly. For the latest information, visit the Cybersecurity and Infrastructure Security Agency at https://www.cisa.gov.
Other references:
https://www.dodcui.mil/Home/Training/
https://securityawareness.usalearning.gov/cui/index.html
https://www.dodcui.mil/CUI-Registry-New/
https://www.dodcui.mil/Frequently-Asked-Questions/